Requirements (self-hosted Nest)
This page describes the network architecture and connectivity requirements when self-hosting Nest.
Architecture
The following image depicts the involved components and their connectivity flows. To illustrate it with examples, we have chosen the 10.0.0.0/8 RFC1918 range and the domain company.local as an example – please adapt it to your setup.
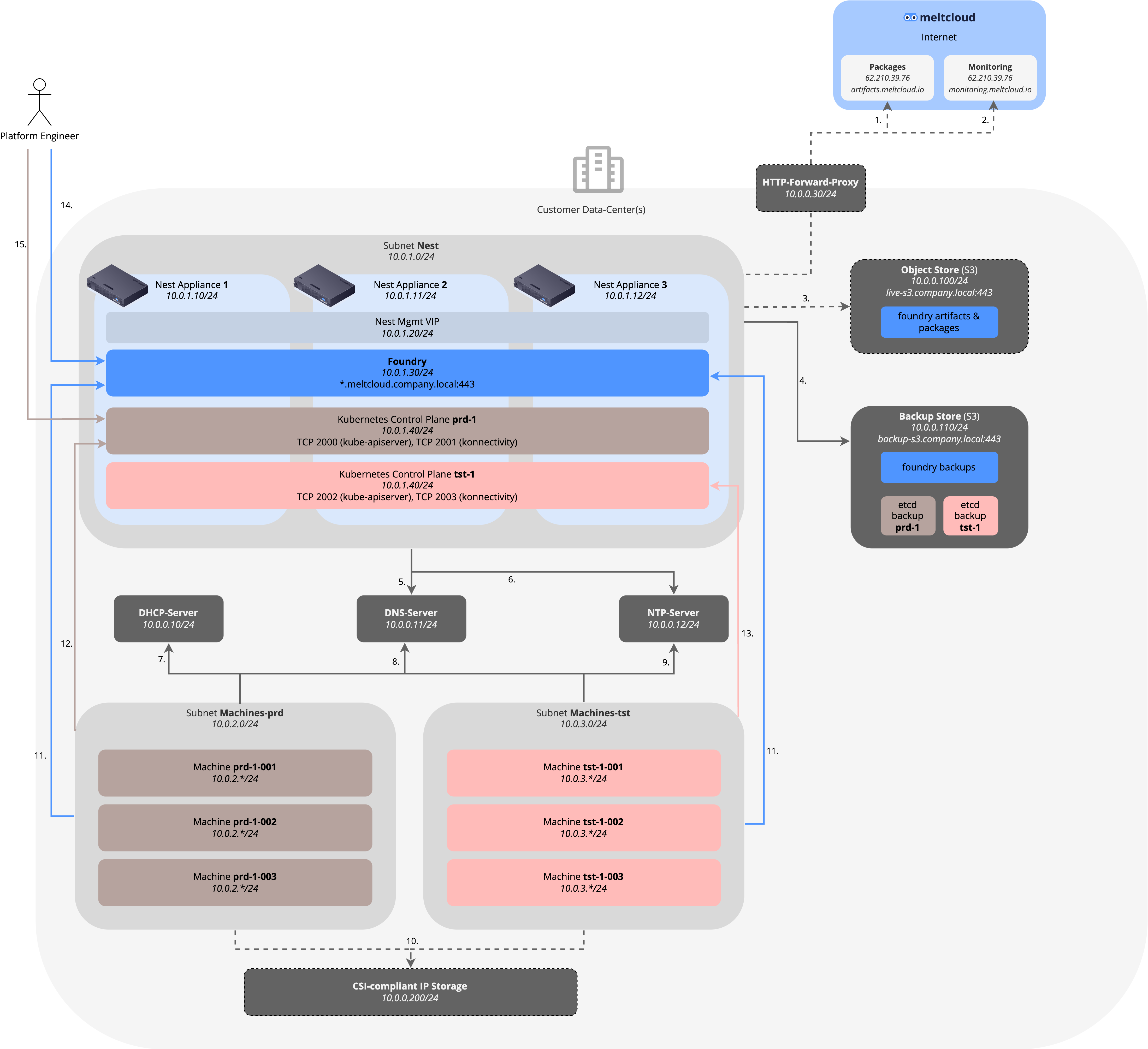
Customer-provided Services
As shown in the picture above, meltcloud requires the following services to be provided by the customer:
- DHCP-Server: to provide IP addresses, routes, DNS & NTP servers for all Machines. See Details below for the required fields. Nest itself doesn't use DHCP and is statically addressed.
- DNS: to register the internal hostnames (
*.meltcloud.company.local) and to resolve all internal and external destinations - NTP-Server: to synchronize time of Machines. Strongly recommended to avoid issues with TLS client certificates. If none provided, Machines will fall back to
*.flatcar.pool.ntp.org. - Object Store (S3): optional, to store Foundry artifacts and packages (to avoid storing them on the Nest appliance)
- Backup Store (S3): to store Foundry and Control Plane backups for disaster recovery purposes
- Egress Internet Connectivity (unless Airgapped): Connectivity to
artifacts.meltcloud.ioormonitoring.meltcloud.io. An HTTP forward proxy can be used.
Port Matrix
The following table shows all required connectivity according to the image above:
| ID | Source | Destination | Ports/Protocols | Reason | Required | Comment |
|---|---|---|---|---|---|---|
| 1 | Subnet Nest (10.0.1.0/24) | artifacts.meltcloud.io (62.10.39.76) | 443/tcp (HTTPS) | To download package updates | Yes, unless Airgapped | Dedicated IP (no CDN). HTTP proxy supported. |
| 2 | Subnet Nest (10.0.1.0/24) | monitoring.meltcloud.io (62.10.39.76) | 443/tcp (HTTPS) | To push metrics data for remote support | Yes, unless Airgapped | Dedicated IP (no CDN). HTTP proxy supported. |
| 3 | Subnet Nest (10.0.1.0/24) | live-s3.company.local (10.0.0.100) | 443/tcp (HTTPS) | To store Foundry artifacts on packages | No | To avoid storing large files on Nest. Recommended for bigger setups/when S3 is available in-house. |
| 4 | Subnet Nest (10.0.1.0/24) | backup-s3.company.local (10.0.0.110) | 443/tcp (HTTPS) | To store Foundry and Control Plane Backups for DR | Yes | Can also be consumed as an additional service from meltcloud (if not available in-house) |
| 5 | Subnet Nest (10.0.1.0/24) | DNS-Server (10.0.0.11) | 53/udp/tcp (DNS) | To resolve hostnames | Yes | |
| 6 | Subnet Nest (10.0.1.0/24) | NTP-Server (10.0.0.12) | 123/udp (NTP) | To synchronize time | No | If unset, falls back to *.flatcar.pool.ntp.org |
| 7 | Subnets Machines-* (10.0.2-3.0/24) | DHCP-Server (10.0.0.10) | 67/udp (DHCP) | To retrieve IPs, routes, DNS & NTP server | Yes | |
| 8 | Subnets Machines-* (10.0.2-3.0/24) | DNS-Server (10.0.0.11) | 53/udp/tcp (DNS) | To resolve hostnames | Yes | |
| 9 | Subnets Machines-* (10.0.2-3.0/24) | NTP-Server (10.0.0.12) | 123/udp (NTP) | To synchronize time | No | If unset, falls back to *.flatcar.pool.ntp.org |
| 10 | Subnets Machines-* (10.0.2-3.0/24) | CSI-compliant IP Storage (10.0.0.200/24) | NFS, iSCSI, ... | For persistent volumes | No | Depends on vendor/technology |
| 11 | Subnets Machines-* (10.0.2-3.0/24) | Foundry, *.meltcloud.company.local (10.0.1.30) | 443/tcp (HTTPS) | Agent <> Foundry interaction, downloading of packages | Yes | Uses TLS Client Certificates |
| 12 | Subnet Machines-prd (10.0.2.0/24) | Kubernetes Control Plane prd-1 (10.0.1.40) | 2000/tcp, 2001/tcp (HTTPS) | Kubelet -> kube-apiserver and konnectivity traffic | Yes | Uses TLS Client Certificates; check Web UI for assigned Ports |
| 13 | Subnet Machines-tst (10.0.3.0/24) | Kubernetes Control Plane tst-1 (10.0.1.40) | 2002/tcp, 2003/tcp (HTTPS) | Kubelet -> kube-apiserver and konnectivity traffic | Yes | Uses TLS Client Certificates; check Web UI for assigned Ports |
| 14 | Platform Engineer | Foundry, *.meltcloud.company.local (10.0.1.30) | 443/tcp (HTTPS) | Web or API interaction | Yes | Allow Websockets if going over a HTTP proxy |
| 14 | Platform Engineer | Kubernetes Control Plane prd-1 (10.0.1.40) | 2000/tcp, 2001/tcp (HTTPS) | kubectl interaction | No | Give access to all Clusters as necessary; check Web UI for assigned Ports |
DNS entries & TLS certificates for Foundry
The Foundry requires a.) DNS entries to resolve to its IP (i.e. *.meltcloud.company.local to 10.0.1.30) and b.) a TLS server certificate for the SAN *.meltcloud.company.local.
If you'd rather not use wildcards, you can create DNS entries/SANs for the following hostnames:
app.meltcloud.company.local(used for Web-Browser and Terraform access)agent.meltcloud.company.local(used for Agent -> API access)pkg-push.meltcloud.company.local(used to push local packages for Machines)pkg.meltcloud.company.local(used to read local packages for Machines)
Custom internal CAs are supported.
Machine Network Configuration via DHCP
Machines require DHCP to configure IP addresses and environment-specific settings like routes, DNS and NTP servers.
Through DHCP, the following parameters must be provided:
- IP address and subnet: primary network identity of the host
- Default gateway and static routes: customized routing for specific environments
- DNS servers and search domains: name resolution configuration
- NTP servers: time synchronization sources
Example Kea DHCP configuration
{
"Dhcp4": {
"subnet4": [
{
"subnet": "10.10.10.0/24",
"pools": [
{ "pool": "10.10.10.100 - 10.10.10.200" }
],
"option-data": [
{ "name": "routers", "data": "10.10.10.1" }, // sets default gw / route
{ "name": "domain-name", "data": "lab.example.com" }, // dns search domain
{ "name": "domain-name-servers", "data": "10.10.10.53, 10.10.10.54" }, // dns servers
{ "name": "ntp-servers", "data": "10.10.10.60" }, // ntp source
]
}
]
}
}